Definition of important concepts in integral security
A summary of knowledge and references related to the terms used and their definitions, applied to the topic of integral safety.
2.1.1 Assets
An asset refers to a physical, logical, or cyber entity that determines the structure and behavior of the observed system [6]. The results of studies[1,4] provide lists of identified assets for a model metro station and the control system of the Prague metro (e.g., people, property including technologies, energy, information, and material flows), primarily based on analyses of metro documentation[1,4,10,11]. Considering it is an open system of systems, it is essential to account for additional aspects beyond technical components, such as organizational, financial, functional, logical connections, and more, as discussed in [1,4]. For further analyses, the following asset groups are considered: constructions, technology, personnel, locations, functions, connections and flows, organization, and economy.
2.1.2 Disasters
The causes of risks are disasters of all kinds, referred to as the All-Hazard Approach[12], and in the case of technological systems, risks also arise from fault states caused by random or systematic system errors[4,13]. It is evident from the above that the occurrence of a single extreme disaster can trigger a chain of additional disasters, i.e., secondary impacts, or even an entire cascade of effects. Secondary, tertiary, and further impacts are referred to as indirect impacts. The indirect impacts of extreme disasters are illustrated in Figure 1. Figure 1 shows the interconnectedness of the impacts of an extreme disaster with various protected assets, leading to additional impacts on other assets, i.e., indirect impacts, which take the form of cascades (i.e., the cascading effect).
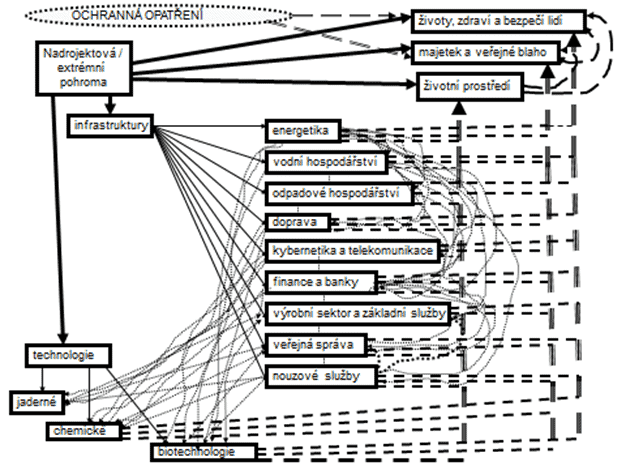
Based on the magnitude of damages and losses to public assets and the probability of occurrence—i.e., through analysis and risk assessment using the risk matrix method as per [13]—disasters in safety management can be categorized into three categories:
- Critical disasters: may trigger a critical situation in the monitored area or its parts, during which, according to current Czech legislation, a state of emergency may be declared, requiring the restoration of property following the emergency. From a safety management perspective, preventive and mitigating measures must be implemented in urban planning, design, construction, and operation of civil and technological facilities as well as infrastructure.
- Specific disasters: can trigger emergency situations, and therefore, response and preparedness (mitigation measures) must be accounted for. From a safety management perspective, preventive measures must be taken in land planning, design, construction, and operation of civil and technological buildings as well as infrastructure, and mitigating measures must be implemented as part of response preparedness.
Relevant disasters: all other disasters that may affect the entity and are neither critical nor specific. They should be managed with standard means, i.e., prevention carried out in practice. From a safety management perspective, the measures already implemented in land planning,
- design, construction, and operation of civil and technological buildings as well as infrastructure are sufficient, and therefore, only regular checks of their effectiveness are necessary.
For the purposes of the presented dissertation, the following disasters were used, identified in the work [4] by analyzing archival documents of the City of Prague [15]:
Results of processes occurring inside and outside the Earth: flood, storm, earthquake, liquefaction of the substrate, gas eruption to the Earth’s surface.
Results of processes in the human body, human behavior, and processes in human society: epidemic, pandemic, breakdown of societal stability, attack, terrorist attack, attack using chemical, nuclear, radiological, and biological (CBRNE) weapons, armed conflict, war.
Results of processes and activities installed by humans: industrial accident, accident during the transport or storage of hazardous substances, transportation accident, disaster in the area of critical infrastructure, disaster in the economy, disaster in territorial infrastructure, disaster in cyber infrastructure, disaster in service infrastructure, supply and communication, technology failure, loss of serviceability.
Interaction of the planet Earth and the environment on human activities: disruption of substrate stability due to vibrations, air contamination, water contamination, rapid climate variations, migration of large groups of people.
Internal dependencies in the human system, natural or human-made: organizational failure, disruption in the flow of raw materials and products, disruption in the flow of energy, disruption in the flow of information.
Table 1 contains the classification of disasters relevant to the City of Prague into categories, details are provided in the work [4]. That is, it considers the All-Hazard-Approach [12,13] and data [15]; details are in the works [12,13,16].
Table 1 Distribution of disasters – relevant, specific, critical.
| Relevant | Specific | Critical | |
| Results of processes occurring inside and outside the Earth | |||
| Flood | yes | yes | yes |
| Storm | yes | yes | |
| Earthquake | yes | ||
| Liquefaction of the substrate | yes | yes | yes |
| Gas eruption to the Earth’s surface | yes | ||
| Results of processes in the human body, human behavior, and processes in human society | |||
| Epidemic | yes | yes | yes |
| Pandemic | yes | yes | yes |
| Breakdown of societal stability | yes | yes | |
| Criminality | yes | yes | |
| Attack | yes | yes | |
| Terrorist attack | yes | yes | yes | Attack using chemical, nuclear, radiological, and biological (CNRB) weapons | yes | yes | yes |
| Armed conflict | yes | yes | yes |
| War | yes | yes | yes |
| Results of processes and activities installed by humans | |||
| Industrial accident | yes | ||
| Accident during transport or storage of hazardous substances | yes | ||
| Accident during transportation | yes | yes | yes |
| Disaster in the area of critical infrastructure | yes | yes | |
| Disaster in the economy | yes | ||
| Disaster in territorial infrastructure | yes | ||
| Disaster in cyber infrastructure | yes | yes | |
| Disaster in service, supply, and communication infrastructure | yes | ||
| Technology failure | yes | yes | yes |
| Loss of serviceability | yes | ||
| Interaction of the planet Earth and the environment on human activities | |||
| Violation of substrate stability due to vibrations | yes | yes | yes |
| Air contamination | yes | yes | |
| Water contamination | yes | yes | |
| Rapid climate variations | yes | ||
| Migration of large groups of people | yes | ||
| Internal dependencies in the human system, natural or human-made | |||
| Organizational failure | yes | yes | yes |
| Failure in the flow of raw materials and products | yes | ||
| Failure in the flow of energy | yes | yes | yes |
| Failure in the flow of information | yes | yes | yes |
2.1.3 Risk and Criticality
The term risk has different and inconsistent interpretations in many areas; some definitions of risk are based on probability, while others focus on expected value or uncertainty [17]. In project management and management systems, risk is generally defined as “the effect of uncertainty” [18]. The effect of uncertainty, if it materializes, can have both negative and positive characteristics (i.e., opportunities) [18].
Risk in engineering fields such as system risk management, reliability management, and safety risk management expresses the probable magnitude of unacceptable (i.e., undesirable) consequences (losses, damages, and harm) of a disaster of a certain threat level (i.e., the normative potential of the disaster) on protected interests (assets) within a specified time interval in a given location [17].
The sources of these risks are the disasters mentioned in the previous paragraph. These risks are for people, their property, the environment, critical infrastructure, and, last but not least, for the state. Risks can be classified according to the chosen protected assets and whether a single protected asset (i.e., partial risk) or a set of protected assets (integrated risk) or a set of protected assets and the connections and flows between them (complex risk / integral risk) is considered.
Furthermore, risks are divided based on which disasters or sources of disasters are considered (only certain disasters, some of their scenarios, or all relevant disasters, etc.).
In common practice, and particularly in transportation systems, partial and integrated risks are typically considered, which are expressed as the product of the probability of occurrence of a disaster (or incident or failure) or frequency of occurrence and the magnitude of their consequences (losses, damages, harm) on the monitored entity or selected set of entities. There are many possible variables for calculating risk depending on the area being considered, but they usually involve the product of the two mentioned. In more detailed studies, the degree of vulnerability is considered, and sometimes the degree of controllability of harmful events; for example, in the automotive industry [19].
Thus, in the understanding of risk (R), we observe many differences, with the only common factor being that risk arises from concerns about an uncertain future [5,17]:
R = frequency ∙ consequences;
R = severity ∙ probability of occurrence;
R = threat ∙ vulnerability;
R = threat ∙ vulnerability ∙ impacts;
R = threat ∙ vulnerability / capacities;
R = (threat ∙ vulnerability) / countermeasures ∙ impacts;
R = f (threat ∙ vulnerability / capacities);
R = f (assets (protected interest) ∙ threat ∙ vulnerability);
R = frequency ∙ population ∙ vulnerability.
To ensure the safety of an area, or larger technological units or facilities, it is necessary to account for complex risk, i.e., integral risk based on a systemic approach to reality [2]. Integral risk involves multiple protected assets, including life, health, and safety of people, property, public welfare, the environment, technologies, and infrastructure, and also includes the influence of interconnections between these protected assets (in English, interdependences) [4,17].
The integral risk, denoted as R, is for all disasters in the area given by the relation [17]:

(1)
Rk expresses the risk for the k-th disaster:

(2)
Pk denotes the probability of occurrence of the k-th disaster, and Di,k denotes the impact of the k-th disaster on the i-th protected interest. Similar relationships apply to integrated risk, but with the difference that for integral risk, the impacts Di,k also include not only direct impacts DDi,k but also indirect (secondary, tertiary, and more) impacts DIi,k, whose relationships, according to the source [19], are as follows:
(3)
Vi is the value of the protected interest, S is the monitored area or object, Zi,k is the vulnerability of the i-th protected interest during the k-th disaster, Ii,k is the function of mutual dependencies (interdependences). The mutual dependencies depend on the specific structure of protected interests in the area and specific connections between protected interests and the disaster, i.e., according to [17]:

(4)
VDk is the characteristic of the degree of the k-th disaster, which affects the impacts on protected assets. VPi,k is the characteristic of the degree of mutual connectivity of protected interests in the given area. The determination of VPi,k is the subject of detailed research based on Boolean logic or, in the case of more complex dependencies, operational analysis methods [17,19,20].
For technical systems [21] the relation applies:

(5)
where H is the threat associated with the given disaster at the object location; Ai are the values of monitored assets for i = 1,2,…, n; Zi are the vulnerabilities of the assets for i = 1,2,…, n; F is the loss function; Pi are the probabilities of asset damage occurrence for i = 1,2,…, n – these are conditional probabilities; O is the vulnerability of protective measures; S is the size of the monitored object; t is the time measured from the occurrence of the harmful event; T is the time during which losses occur; and t is the period of recurrence of the disaster. Since the loss function is typically not known, failure scenarios are created and multicriteria methods are used to assess the risk; typically, decision support systems [22].
From the above knowledge and given the complexity of the systems, it is clear that integral security can only be increased by considering and managing integral risks, which do not only consider the sum of partial risks but also account for dependencies and flows between assets [13].
For safety management purposes, the criticality of an asset (K) is understood as the function of the importance and vulnerability of the monitored asset or even the entire entity, expressed as the product of [13,17]:
K = importance ∙ vulnerability (6)
Criticality with regard to a certain disaster can be expressed by the relation
C = S ∙ O ∙ B (7)
where S is the severity of the largest impact of the disaster (harmful event), O is the probability of the disaster occurrence, and B is the conditional probability that the most severe impact will occur [13,23]].
Risk, as mentioned in the introduction of this section, refers to the effect of uncertainty, i.e., how frequently (or probably) extensive losses will occur. By reducing risk, we reduce the frequency of unfavorable events (if it is within our power) or their impacts. Risk thus relates to safety but is not defined by safety. Criticality refers to the threshold value between two states, in the area of safety it is the undesirable (danger) and desirable (safety). By reducing criticality, i.e., the threshold between danger and safety, we increase the state space of the system in the safe area, i.e., we increase safety. Therefore, criticality is a complementary variable to safety, even though it is a result of risk factors and may have the same input parameters as risk (e.g., vulnerability) [27].
2.1.4 Security
In current practice, the term “safety” has several different meanings. In transportation systems, the term is associated with: the protection of people without considering the system’s interdependencies; the system’s resilience against disruption from an adverse event (disaster); or against internal errors. In connection with protective or security systems, safety is understood as so-called functional safety, i.e., the realization of a safe function or process in the case of anticipated situations [24]. In reality, these meanings have the same goal: to protect human health and life and to ensure the development of human society. In other words, all these meanings are part of integral safety, which brings them all together.
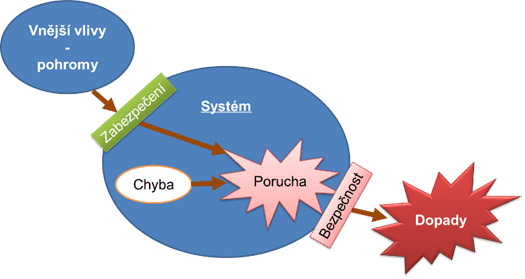
System safety in the context of integral safety means that the system is protected against both internal and external disasters, including human factors. That is, the system has sufficient resilience and adaptability to expected conditions. Additionally, a safe system must not endanger its surroundings even under critical conditions [20,25,26,27], Figure 2 according to [20].
The potential impacts of system failures, as shown in Figure 2, will manifest in other systems as a disaster in their vicinity, creating a chain of disasters, i.e., a cascading effect.
The term “safety” (Safety) according to current knowledge refers to a set of means and measures by which humanity ensures its security (English: Security) and sustainable development (English: Sustainable Development). In Figure 3, the concept focused on safety is depicted, i.e., on a higher goal; it is not just about reducing risk, but about increasing the safety of people and other public assets on which people depend [27].
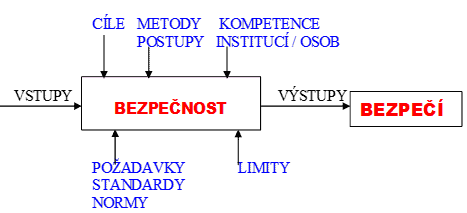
From the above, it follows that safety and risk are related, but they are not complementary quantities, because safety can be increased by organizational measures that do not affect the size of the risk. Criticality is a complementary quantity to safety. By reducing the criticality, we increase the safety of the monitored object.
2.1.5 Human safety and integral safety
- Economic security (persistent poverty, unemployment),
- Food security (hunger, famine),
- Health security (deadly infectious diseases, unsafe food, malnutrition, lack of basic healthcare),
- Environmental security (environmental degradation, resource depletion, natural disasters, pollution),
- Personal security (physical violence, crime, terrorism, domestic violence, child abuse),
- Political security (ethnic, religious, and other identity-based tensions),
- Community security (political repression, abuse of human rights).
- Place safety (e.g., layout, environmental management, emergency procedures, fire safety measures, first aid, lighting, social infrastructure).
- Process safety (e.g., physical security, emergency stop elements, “fail-safe” principles, perimeter protection).
- Human resource safety (e.g., safety training, personal protective equipment, supervision, medical check-ups).
2.1.6 Critical infrastructure and its security
- Energy supplies (electricity, gas, heat, oil, and oil products).
- Water (provision of drinking and utility water, securing and managing surface and groundwater sources, wastewater systems).
- Food supply and agriculture (food production, food care, agricultural production).
- Healthcare (pre-hospital emergency care, hospital care, public health protection, production, storage, and distribution of pharmaceutical products and medical devices).
- Transport (road, rail, air, and water).
- Cyber, communication, and information systems (fixed and mobile telecommunication network services, radio communication and navigation, television and satellite communication, postal and parcel services, internet, and data services).
- Banking and financial sector (public finance management, banking, insurance, capital market).
- Rescue system (Czech Fire Rescue Service, fire protection units, Czech Police, Czech Army, radiation monitoring, forecasting, warning system, etc.).
- Public administration (state administration and self-government, social security and employment, state social support and social assistance, administration of the judiciary and prison system).
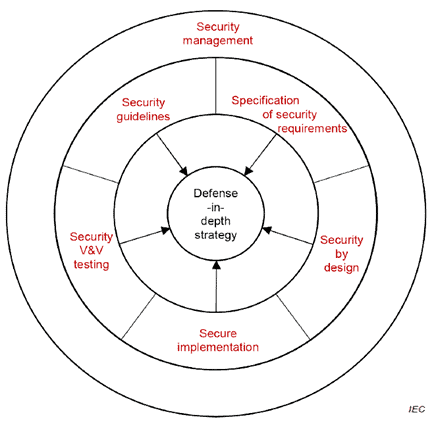
2.1.7 Modern approaches: All-Hazard-Approach and Defense in Depth
- security directives,
- security requirements specifications,
- security by design,
- secure implementation,
- security verification and validation,
- Defence-In-Depth strategy.
2.1.8 Systems of systems (SoS), project and over-project phenomena
- autonomy – autonomy is exercised by the constituent systems to fulfill the purpose of the global system, i.e., SoS,
- affiliation – individual constituent systems choose their affiliation based on the ratio of costs and benefits to fulfill their own purpose and in belief of the supra-purpose of SoS; in the classical system concept, affiliation is determined by their nature and cannot be arbitrarily changed (e.g., as a member of one family),
- connectivity – countless possible interconnections of systems and their parts to enhance the capabilities of SoS,
- diversity – higher diversity in the capabilities of SoS achieved through the autonomy of different constituent systems, their chosen affiliation, and open connectivity,
- emergence – in the SoS concept, the increased intentional unpredictability of the system and the creation of conditions for the possibility of emergence (i.e., the emergence) is of crucial importance in both negative (emergence of unpredictable negative events, disasters) and positive (early detection and elimination of adverse system behaviors) aspects.
- desired: improve the properties of systems, devices, and infrastructures,
- undesired:
- lead to system losses,
- cause systems to fail to properly perform their functions,
- cause systems to endanger themselves and their surroundings.

